The Intersection of Artificial Intelligence and Embedded Security: A Promising Future
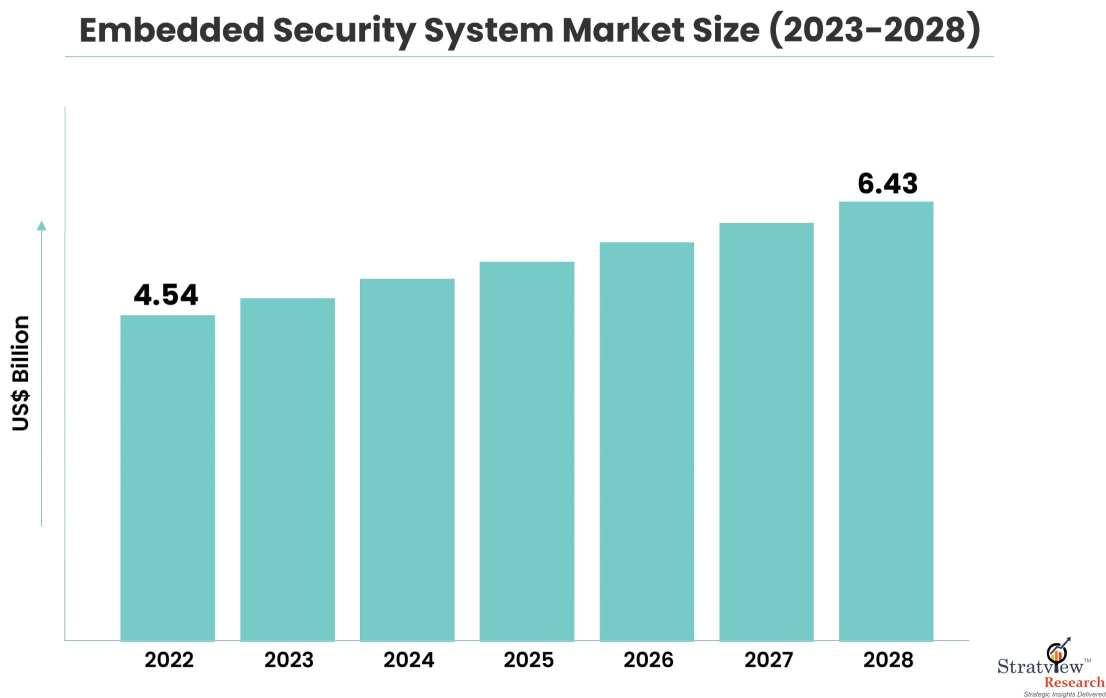
In recent years, the world has witnessed remarkable advancements in both artificial intelligence (AI) and embedded systems. AI, the simulation of human intelligence in machines, has rapidly permeated various industries, while embedded systems have become the backbone of countless devices and technologies we rely on daily. The convergence of these two cutting-edge fields has given rise to a promising future, where the fusion of AI and embedded security is revolutionizing how we approach cybersecurity, protect sensitive data, and ensure the integrity of critical systems. The embedded security system market is estimated to grow from USD 4.54 billion in 2022 and is likely to grow at a CAGR of 5.93% during 2023-2028 to reach USD 6.43 billion by 2028.
Understanding Embedded Security:
Embedded systems refer to specialized computing systems designed to perform dedicated functions within larger systems or devices. These systems are present in a vast array of applications, ranging from consumer electronics like smartphones and smart home devices to industrial machinery, automotive systems, healthcare devices, and more. Due to their widespread use and critical functions, securing embedded systems against cyber threats is of paramount importance.
Traditionally, embedded security has relied on encryption, firewalls, and various hardware and software mechanisms to protect against known vulnerabilities. However, the rapidly evolving threat landscape demands a more proactive and adaptive approach. This is where artificial intelligence steps in to play a transformative role.
AI Empowering Embedded Security:
AI possesses the unique ability to analyze vast amounts of data, recognize patterns, and learn from its experiences, enabling it to make informed decisions and predictions. These characteristics can significantly enhance embedded security in multiple ways:
Threat Detection and Mitigation: AI algorithms can continuously monitor embedded systems, analyzing network traffic, system behavior, and user interactions in real-time. They can quickly identify abnormal activities and potential threats, even those previously unknown, thereby mitigating risks before they escalate.
Anomaly Detection: One of the essential aspects of embedded security is the ability to detect anomalous behavior. AI models can establish baseline behavior patterns and flag deviations from these norms, enabling early detection of potential security breaches or malfunctions.
Predictive Maintenance: In industrial settings, predictive maintenance is crucial for preventing system failures and reducing downtime. AI-powered embedded systems can analyze sensor data and anticipate when maintenance is required, ensuring optimal performance and preventing security vulnerabilities arising from neglected maintenance.
Firmware and Software Security: AI can assist in identifying and patching security vulnerabilities in firmware and software that run on embedded systems. Through continuous analysis of code and runtime behavior, AI can recognize potential weaknesses and suggest improvements to bolster security.
Biometric Authentication: As biometric authentication becomes more prevalent, AI-driven systems can offer enhanced security by efficiently recognizing and verifying users based on unique physiological or behavioral characteristics.
Secure Communication Protocols: AI can optimize communication protocols between embedded devices, ensuring secure data transmission and reducing the likelihood of interception or manipulation.
Challenges and Ethical Considerations:
While the integration of AI and embedded security promises a bright future, it also comes with certain challenges and ethical considerations:
Data Privacy Concerns: AI's effectiveness relies heavily on data analysis, raising concerns about data privacy and potential misuse of sensitive information. Striking a balance between data utilization and privacy protection will be crucial.
AI Bias: AI algorithms are only as good as the data they are trained on. Bias in data can lead to biased decisions, which may impact security measures differently for various user groups.
Adversarial Attacks: AI itself can be vulnerable to adversarial attacks where malicious actors exploit AI's weaknesses to deceive security systems.
Regulatory Frameworks: As AI becomes more integrated into embedded systems, robust regulatory frameworks will be necessary to ensure its responsible and ethical use.
Conclusion:
The intersection of artificial intelligence and embedded security holds immense promise for a more secure and resilient future. With AI's analytical power and adaptability, embedded systems can proactively defend against ever-evolving cyber threats, safeguard sensitive data, and ensure the smooth operation of critical infrastructure. However, to fully unlock its potential, we must address the challenges and ethical considerations, forging a path where AI and embedded security work hand in hand to create a safer and more connected world.
- Art
- Causes
- Crafts
- Dance
- Drinks
- Film
- Fitness
- Food
- Jeux
- Gardening
- Health
- Domicile
- Literature
- Music
- Networking
- Autre
- Party
- Religion
- Shopping
- Sports
- Theater
- Wellness
- IT, Cloud, Software and Technology


